Anti-bot services used by PhaaS - Part 1
Phishing-as-a-Service (PhaaS) kits will frequently employ one or more techniques to avoid detection by security software. Often they will use a captcha like Cloudflare Turnstile, Google reCAPTCHA, or even their own captcha. Another one of the methods used is to leverage another service called an anti-bot service. These paid services offload the work required to differenciate between potential victims and malware security scanning. The PhaaS operator may advertise their anti-bot capabilities as part of their services, which is actually their use of these separate services.
Here I will describe one such service offered by Adspect and used by Mamba2FA.
Adspect
Adspect is a service that offers to detect and block unwanted visitors in web traffic.
Adspect blocks all kinds of website checkers: Google Safe Browsing, VirusTotal, Kaspersky, BrandVerity, GeoEdge, AdSecure, The Media Trust, Confiant, Ad Lightning, etc.
 |
|---|
| Adspect main web page |
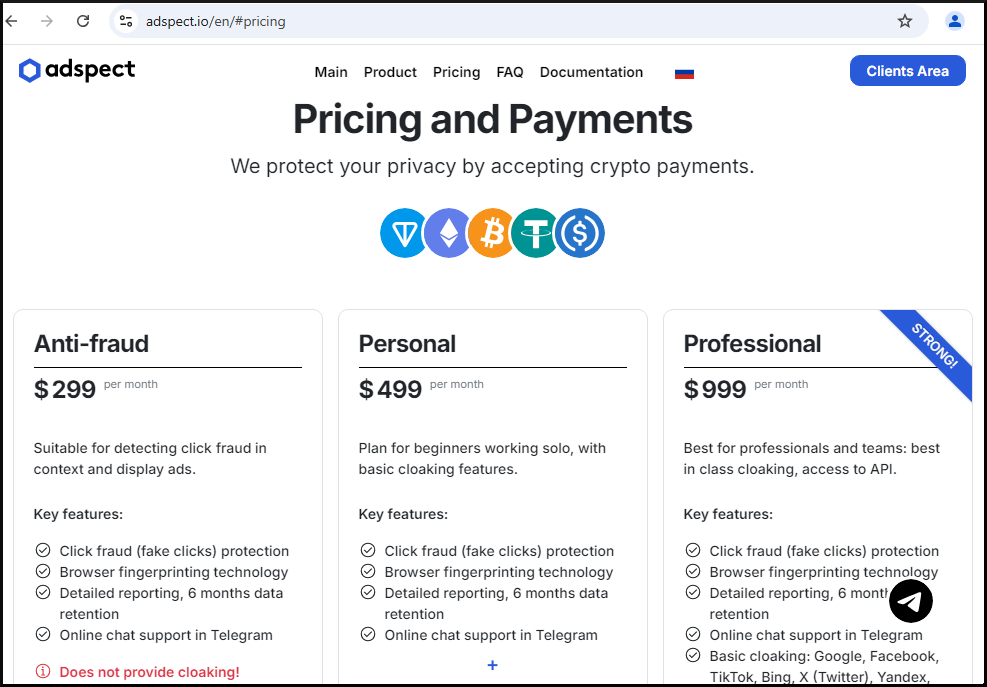 |
|---|
| Adspect pricing |
Mamba2FA
Mamba2FA is a PhaaS that employs the use of Adspect to help avoid detection. This can be seen in action with urlscan. When scanned by urlscan.io, a redirection to Google occurs because Adspect detected it.
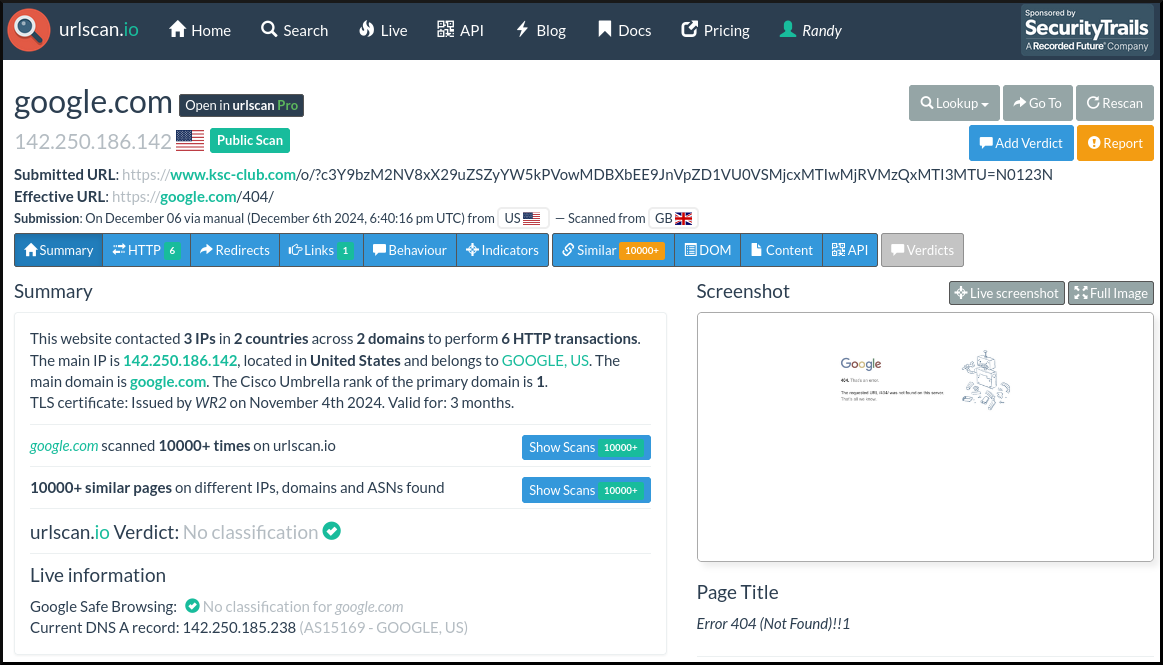 |
|---|
| urlscan.io results for Mamba2FA site www.kcs-club[.]com |
Whereas, visiting the same Mamba2FA URL using an unprotected sandbox from a consumer IP results in the fake Microsoft login being shown.
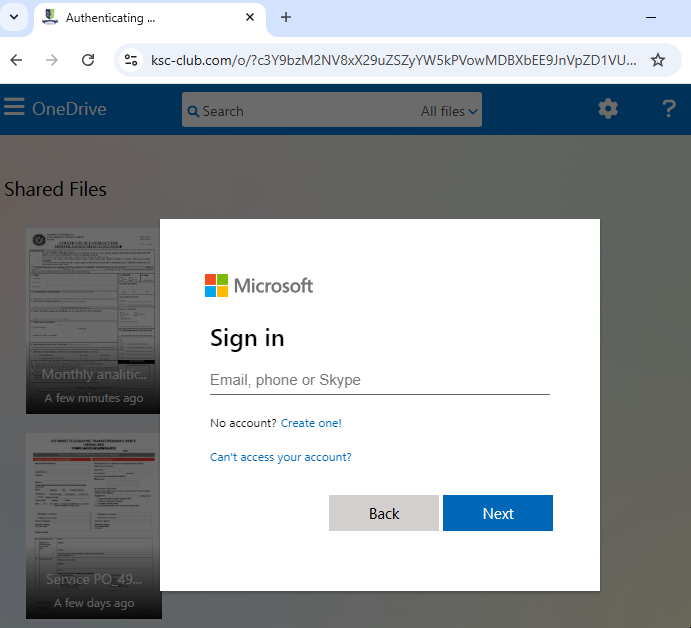 |
|---|
| Fake Microsoft login at www.kcs-club[.]com |
Mamba2FA integration of Adspect
Mamba2FA uses Adspect by creating a stream, downloading a PHP hardcoded for that stream, and referencing that PHP from their index page.
The type of integration used is called Reverse PHP Integration. Here is the Adspect documentation about it.
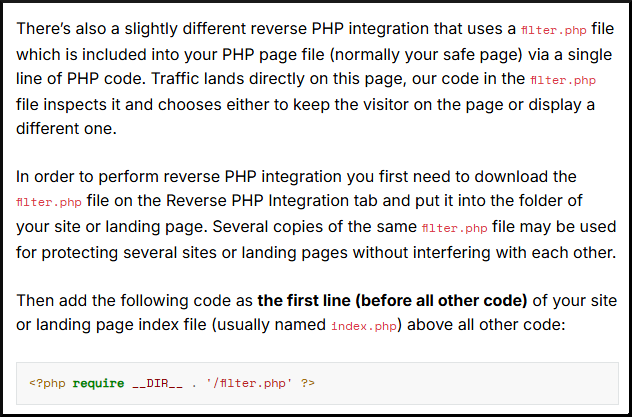 |
|---|
| Adspect documentation on reverse PHP integration |
Here is the top portion of a recent Mamba2FA index.php. The first line is a require
of the PHP downloaded from Adspect. It’s purpose here is to
control whether or not the remainder of this page is executed.
Of note is that Mamba2FA renamed filter.php to i.php.
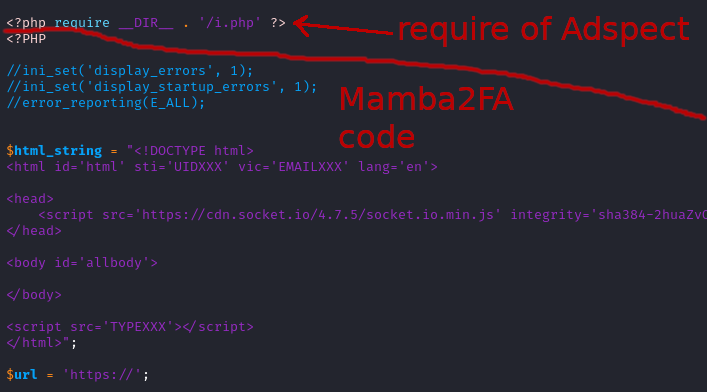 |
|---|
| Mamba2FA index page |
Adspect filter.php
Let’s look at the Adspect filter.php file. While Mamba2FA may have
renamed the file, I’ll still refer to it as filter.php.
Starting at the bottom of the file we’ll see something familar to those
who analyze Mamba2FA. The HTML shown here is what
is initially returned when visiting a Mamba2FA URL. Notice the
<?php exit; on the last line. That is why the remainder of index.php
is not used on the initial access.
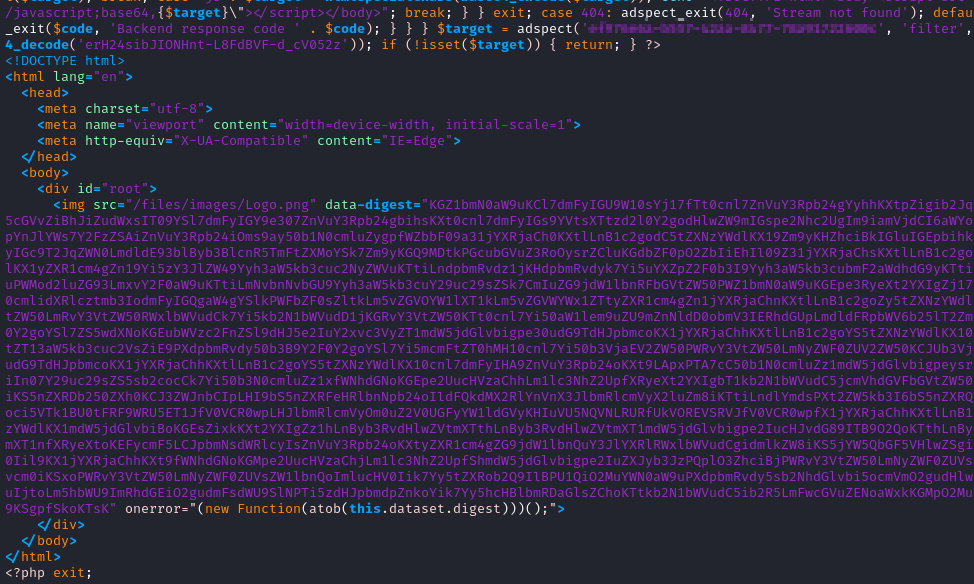 |
|---|
| Adspect filter PHP bottom |
To confirm, looking at the first response for the same urlscan from earlier we see the very same HTML.
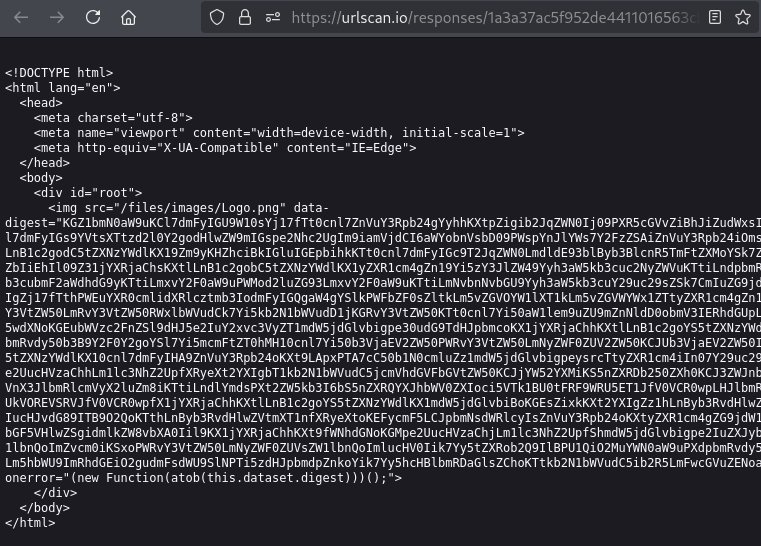 |
|---|
| urlscan.io response |
So, the initial response from Mamba2FA isn’t actually Mamba2FA, but instead is code from an Adspect file residing on the Mamba2FA server.
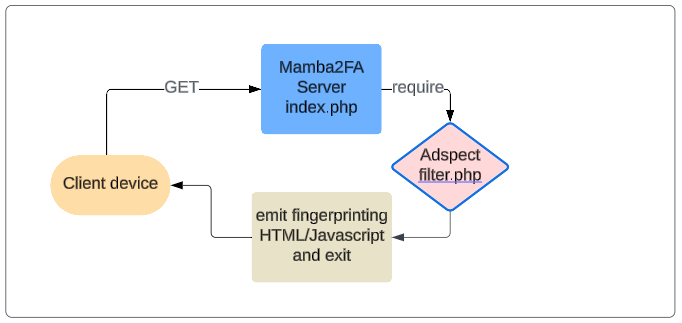 |
|---|
| Fingerprinting flow |
Fingerprinting
There is Javascript hidden with base64 inside the <img> tag.
Because the src refers to a non-existent file, it will cause
the onerror to execute it. It then fingerprints the browser
by gathering Javascript globals such as screen, window, and navigator.
It takes that information and sends it with a POST to the same
original URL.
Here is a top snippet of the POST data after being urldecoded and beautified.
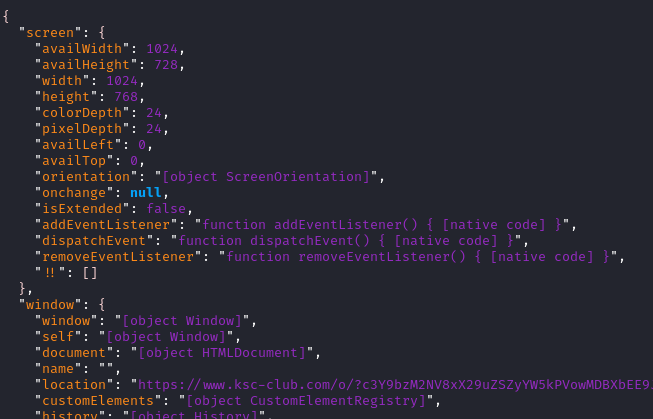 |
|---|
| POST data |
API
The POST’d data will make it’s way back to filter.php.
This time because it has the fingerprint data, the Mamba2FA
server will issue an API call to the Adspect URL
https://rpc.adspect.net/v2/ with the fingerprint data
as well as details like the public IP of the victim and
their browser’s User-Agent. This combined information will
be used by Adspect to decide if the requestor is a bot or a real person.
When the PhaaS operator is in their Adspect portal, they need to create a “stream”. This is a configuration that allows them to control and decide how they would like Adspect to behave. That stream will have a Stream ID or sid in UUID4 format. The sid is how Adspect associates the API call with the PhaaS operator account and desired configuration.
Here is a portion of filter.php that executes the API call.
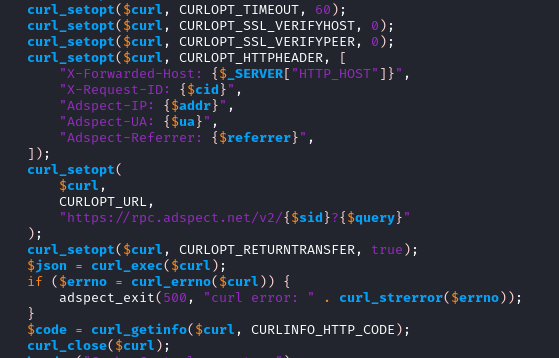 |
|---|
| Adspect API call |
Adspect has a variety of actions it can take. In the case of
Mamba2FA, if it decides you are a bot, it will redirect to
https://google.com/404. Otherwise the filter.php will
just pass through and the remainder of index.php will be
used to render a fake Microsoft login.
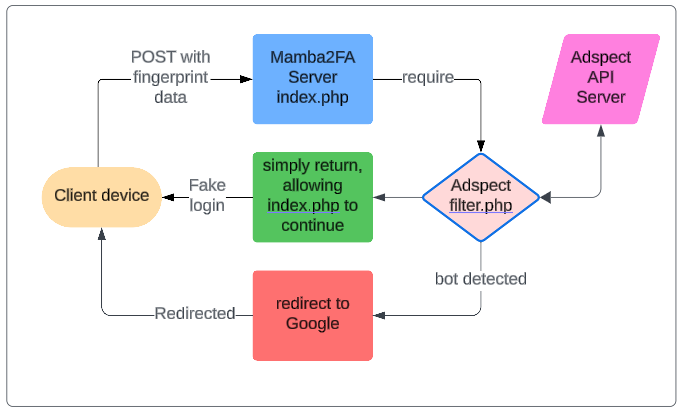 |
|---|
| Decision making flow |
Next Up
Part 2 covers Tycoon2FA usage of BlackTDS.
IOCs
www.kcs-club[.]com
rpc.adspect[.]net
Acknowledgements
Several other collaborators were critical to the discovery of the connection between Mamba2FA and Adspect.
References
https://blog.sekoia.io/mamba-2fa-a-new-contender-in-the-aitm-phishing-ecosystem/
https://www.ironnet.com/blog/robin-banks-still-might-be-robbing-your-bank-part-2